#Ubuntu truecrypt
Explore tagged Tumblr posts
Text
Ubuntu truecrypt

#Ubuntu truecrypt how to
#Ubuntu truecrypt cracker
#Ubuntu truecrypt plus
In Ubuntu 16.04, development packages of wxWidgets 2.8 are no longer available. create-keyfile FILEPATH Create a new keyfile containing pseudo-random data. If at any step the hidden volume protection is triggered, start again from 1). 5) Mount the new filesystem and fill it with data. Besides those improvements, there are no attempts to change the crypto or continue development in any significant way. 4) Create a filesystem on the virtual device of the outer volume.
#Ubuntu truecrypt plus
You can also choose another character encoding and try again. deb of TrueCrypt 7.1a, plus a few patches that fixes minor issues. If you continue editing this file you could corrupt this document. The file you opened has some invalid characters. It works on Linux and it is optimized for Nvidia Cuda technology.
#Ubuntu truecrypt cracker
GitHub - lvaccaro/truecrack: TrueCrack is a brute-force password cracker for TrueCrypt (Copyrigth) volumes. "There was a problem opening the file /home/(removed username)/.cach…/truecrypt-7.1a-setup-x86. TrueCrack is a brute-force password cracker for TrueCrypt (Copyrigth) volumes. Once the bar indicating the progress finishes, I get this: It runs it in "Text Editor" for some reason. This implementation supports mapping (opening) both system and normal TrueCrypt volumes, as well as opening hidden volumes and opening an outer volume while. I selected the standard option, downloaded & clicked the "Truecrypt setup" and it ran its thing in "Archive Manager" (That's what it was set to open the file with by default). There’s a PPA which contains the TrueCrypt package with the tray icon replaced by a application indicator, so that you can get back the TrueCrypt indicator applet in Ubuntu 13.04 panel since the tray icons is no longer supported. I have Ubuntu 10.10 and Windows 7 with TrueCrypt as a.
#Ubuntu truecrypt how to
I double checked the type (32 or 64) to make sure I downloaded the correct one. This simple tutorial shows you how to install TrueCrypt as well as its indicator applet in Ubuntu 13.04 Raring Ringtail. I have now been searching days for a solution but have found nothing. So, I should be able to just run the download as I did before, right?Įdit: Ok, scratch that. I let the updates run themselves, so we're up to speed. Veracrypt is available for Linux, Windows, and MacOS. Ubuntu is successfully installed.although its kind of strange that it doesn't have the "multiple user interface" thing that it had in 12.04.1. VeraCrypt is a fork of TrueCrypt which is a free and open source on-the-fly disk encryption (OTFE) tool.

0 notes
Text
Установка VeraCrypt в Ubuntu 20.04
VeraCrypt - наследник широко известной программы TrueCrypt, разработка которой была свёрнута в 2014 году по загадочным причинам. Используется для шифрования "на лету", позволяет создавать криптографические контейнеры и многое другое. Приступаем: Откр... Читать дальше »
1 note
·
View note
Text
#5yrsago Mysterious announcement from Truecrypt declares the project insecure and dead
The abrupt announcement that the widely used, anonymously authored disk-encryption tool Truecrypt is insecure and will no longer be maintained shocked the crypto world--after all, this was the tool Edward Snowden himself lectured on at a Cryptoparty in Hawai'i. Cory Doctorow tries to make sense of it all.
The Sourceforge project page for Truecrypt now sports a cryptographically signed notice that Truecrypt should no longer be used as it is not secure. The news came on the heels of a crowdfunded $70K security audit of the open source, anonymously maintained software giving it a relatively positive initial diagnosis. The announcement -- signed by the same key that has been used to sign previous, legitimate updates -- links Truecrypt's deprecation to Microsoft's decision to cease supporting Windows XP, though no one seems to have a theory about how these two facts relate to one another.
WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues. This page exists only to help migrate existing data encrypted by TrueCrypt. The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.
Truecrypt is a widely used system for disk-encryption, and is particularly noted for its "plausible deniability" feature, through which users can create hidden partitions within their cryptographic disks that only emerge if you enter the correct passphrase; this is meant to be a defense against "rubber hose cryptanalysis," in which someone is physically or legally threatened in order to coerce them into yielding up her keys. In the "plausible deniability" scenario, the victim can give up the keys to a "harmless" partition while keeping the very existence of a second partition for sensitive material a secret. I am a Truecrypt user, as, apparently, is Edward Snowden, who lectured on the software's use at a Cryptoparty he held in Hawai'i before going on the run.
The response to the Truecrypt news is mostly frank bafflement. The software is licensed under an obscure "open source" license that makes it unclear whether third parties can support the now (apparently) orphaned codebase.
Matthew Green, a Johns Hopkins University Information Security Institute crypto researcher, is the experts who led the fundraising in order to audit the Truecrypt source; in an interview with Brian Krebs, he says that he intends on continuing the work:
“There are a lot of things they could have done to make it easier for people to take over this code, including fixing the licensing situation,” Green said. “But maybe what they did today makes that impossible. They set the whole thing on fire, and now maybe nobody is going to trust it because they’ll think there’s some big evil vulnerability in the code.”
Green acknowledged feeling conflicted about today’s turn of events, and that he initially began the project thinking TrueCrypt was “really dangerous.”
“Today’s events notwithstanding, I was starting to have warm and fuzzy feelings about the code, thinking [the developers] were just nice guys who didn’t want their names out there,” Green said. “But now this decision makes me feel like they’re kind of unreliable. Also, I’m a little worried that the fact the we were doing an audit of the crypto might have made them decide to call it quits.”
Whether or not volunteer developers pick up and run with the TrueCrypt code to keep it going, Green said he’s committed to finishing what he started with the code audit, if for no other reason than he’s sitting on $30,000 raised for just that purpose.
The recent Heartbleed vulnerability demonstrated that even code that is widely used and widely examined can harbor long-lived critical bugs. As Green points out, the spectacular and mysterious blow-off from the anonymous Truecrypt team means that even if the code is given a clean bill of health from its auditors, it may be hard to convince people to trust it ever again.
Truecrypt's own warning suggests that users try Bitlocker, the proprietary Microsoft full-disk encryption tool that relies on the on-board Trusted Computing Module to attain a high degree of security. Microsoft itself has a deservedly poor reputation for standing up to government demands to weaken its products' security, but Peter Biddle, one of the architects of Trusted Computing and Bitlocker, has previously told me that he was repeatedly approached by frustrated federal agents who couldn't decrypt Bitlocker partitions, and I believe him, based on my personal knowledge of his character and work.
The free/open source world has some good solutions, like LUKS and dm-crypt, both of which come pre-installed on popular GNU/Linux versions like Ubuntu. The Ubuntu installer has a nice front-end to this stuff, allowing you the option of encrypting your whole disk while you install your OS.
In the meantime, the cause of the shutdown remains a mystery. This Reddit netsec thread is full of juicy speculation about the cause and suggestions for alternatives to Truecrypt.
I'd be interested in hearing your thoughts on alternatives to Truecrypt, and your overall data-security practices. Do you have a "plausible deniability" strategy for your own sensitive data?
https://boingboing.net/2014/05/29/mysterious-announcement-from-t.html
2 notes
·
View notes
Text
How to install and use veracrypt on Ubuntu 22.04
How to install and use veracrypt on Ubuntu 22.04
VeraCrypt is an open-source data encryption utility to encrypt a drive or the whole system storage. VeraCrypt is the descendent of the obsolete encryption utility named TrueCrypt. VeraCrypt is derived from the source code of TrueCrypt. However, it overcomes the limitations of TrueCrypt. For instance, VeraCrypt is equipped with various encryption algorithms such as AES (Advanced Encryption…
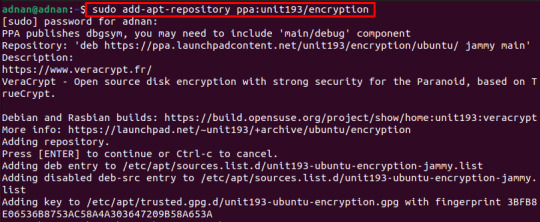
View On WordPress
0 notes
Text
How to create USB password

USB is a small, portable and readable tool. These features make it an excellent means of transferring data between computers. However, because of their mobility, they are more easily lost than ever. Therefore, you should always protect the data contained in the USB. Unfortunately, you can not password protect your USB as you would with a computer or a phone. Your data protection tools work with encryption. If you do not want to invest in a secure flash drive with hardware encryption then you can use the free application to achieve a similar level of protection. The following article will share for you 6 easy ways to set your USB password protection. 1. Save individual files with a password As mentioned, you can not completely protect your USB without using encryption. However, if you're concerned about the time-consuming coding process for the entire directory and need a really quick way to protect only selected files, you can simply save those files with a USB password. . Many programs, including Word and Excel, allow you to save files with a password. For example, in Word, when the document is open, go to File> Info , expand the Protect Document menu, and select Encrypt with Password.

Then, enter the password and confirm it to protect your document.

Finally, save the document and of course do not forget the password you set.

To put a password protected PDF file in USB, you can use PDFTK Builder or its mobile application. 2. Create an encrypted partition and password protected There are many tools that can encrypt and password protect your data. However, most require Administrator privileges to launch on the computer. Such tools are not a viable solution if you need to transfer data securely to a computer where you do not have Administrator rights. Rohos Mini Drive is a tool that will work whether you have Administrator rights or not. Free version can create an encrypted partition and password protected up to 2 GB for your USB. The tool uses automatic encryption with a key length of 256 bits. Thanks to the portable Rohos Disk Browser you install directly on your flash drive, you will not need an encrypted driver on your local system. Then, you can access protected data anywhere.

Click on Encrypt USB drive from start screen of Rohos Mini Drive, select drive, specify a new password and click on Create disk. This will create an encrypted and password protected area on your external drive.

You can open the protected area by clicking the Rohos Mini.exe icon from the root of the USB. After entering the password, Rohos will mount a separate drive and you can access it via File Explorer. To close the Rohos area, right-click the Rohos icon in the Windows Taskbar notification area and select Disconnect. 3. Full USB encryption VeraCrypt is the successor of TrueCrypt . It is a portable application that runs directly from your USB. Unfortunately, it still requires Administrator rights to operate. It uses 256 bit AES encryption. The free version is limited to 2GB drive size. VeraCrypt provides encryption using a variety of algorithms, including 256-bit AES, Serpent and TwoFish, as well as their combination. Like the Rohos Mini Drive, it can create a virtual encrypted drive to mount as a real disk, but you can also encrypt entire areas and storage devices. Download VeryCrypt Portable and install it on your USB. When launching this application, it will show you all the letters of the available disk. Select one and click Create Volume. This will launch the VeraCrypt Volume Creation Wizard.

To encrypt the entire USB drive, select Encrupt a non-system partition / drive and click on Next. In the next step, you can choose from Standard or a Hidden VeraCrypt volume . Using the Hidden VeraCrypt volume will reduce the risk that someone will expose you to a password. Please note that you will format the whole USB if you want to create a Hidden VeraCrypt volume. We will continue with the Standard VeraCrypt volume . In the next window, click on Select Device ... , select your mobile drive, confirm with OK and click on Next.

To encrypt the entire USB drive, select Encrypt partition in place and click on Next. VeryCrypt will warn you that you should have a backup of your data in case something goes wrong during the encryption process. Then, choose Encrypt and Hash Algorithm, you can follow the default settings. Now, you will set the Volume Password . In the next step, random mouse movements will determine the strength of the encrypted cipher. Then select Wipe Mode . In the last window, you click on Encrypt to start coding.

The alternative to VeraCrypt Portable is Toucan, a mobile application that allows you to sync, backup and secure your files. Bonus: Create a password protected archive file Storage tools like 7-Zip can also encrypt and password-protect your files with AES-256. Install and launch 7-Zip, then right-click on the file or folder on your USB drive and select 7-Zip> Add to Archive . In the Add to Archive window , select the Archive format and add a password. Click OK to start the archiving and encryption process.

4. Create Safe Zone on USB with SecurStick SecurStick is a great USB security software. It does not require installation and running on Windows, Linux, Mac without administrative privileges. However, to set it up, you must run the .exe file from the flash drive you want to encrypt. To install SecurStick, download and extract the .zip file, and then copy the .exe file to the USB drive. Running this .exe file will open a command prompt window and browse. Enter the password and click Create to install the Safe Zone.

The next time you open the SecurStick file, a login window to Safe Zone will greet you. Any files you copy into SafeZone are automatically encrypted. Note that closing the console window closes the session on the Safe Zone. The easiest way to completely migrate SecurStick from a flash drive is to reformat it. Download SecurStick Note : The interface of the software home page can be completely switched to English so you easily find out information about it. 5. How to encrypt flash drive on Mac If you're using a Mac, you do not need a third-party tool to encrypt your USB flash drive. First, you need to format the flash drive with Apple's HFS + file system. Note that this will delete the entire archive on it, which means you should back up them. From the Disk Utility , select the flash drive and click Erase. In the popup window, select the file format, MacOS Extended (Journaled), and click Erase at the bottom right to reformat the drive.

Now you are ready to create flash drive encryption. Simply right-click on the drive in the Finder , select Encrypt , and then add the password. This process starts immediately and takes place within minutes, depending on the size of the USB drive. In a nutshell, you will have a USB password protected and encrypted. 6. Encrypt USB drives on Linux with Cryptsetup Cryptsetup is a free feature to set up 256-bit AES-encrypted disks. It is available in the standard Linux repository. Note : You should not use this tool if you intend to use encrypted files outside of Linux. Moreover, access to encrypted flash drives requires the installation of Cryptsetup. To encrypt USB drives on Linux, you need to install the Gnome and Cryptsetup utilities from sudo apt-get . If you use Ubuntu, it's pre-installed on your machine. Next, open Disks from the desktop, find the flash drive and choose to format the drive or partition with the encryption option. At this point, you need to select a password. Note, you must overwrite the whole file. Download Cryptsetup So, you know how to protect your USB in the simple ways mentioned above. You may find this process to be quite time-consuming and unnecessary, but it is really worthwhile to keep the data stored in the USB safe. Read the full article
0 notes
Text
Goodbye, Ubuntu (Story)
So I had a dual-boot setup with Windows 10 as my main OS and Ubuntu 14.04 as my backup. Previously, a Windows 7 update failed with a boot loop and I was stranded with no time to find a way to fix it. Ubuntu was a great help for the time. I learned a lot about Linux, and it booted really fast.
I tried to install Windows 10 technical preview, and it failed. Got stuck at a boot logo. Later, I tried installing Windows 7 and 8.1, both got stuck at the boot logos. I found it unusual that even Windows 7 failed, because the PC came with Windows 7 installed.
But then I finally had the time to look at the virtual recovery disk and it had a pure Windows 7 install optimized for my machine in a Wim format. I had Hiren’s Boot CD which had an app to process Wim files and install them to disk. It was a success, and the best part is, I didn’t have to install the crapware that was on the partition (those were in a separate file, possible a .wim file).
The reason why I finally got around to fixing the Window 7 partition was because I was trying to get it ready for Windows 10. The Windows 10 technical preview (as it was called at the time) didn’t work. It would always get stuck at a logo. After I got Windows 7 working, I transferred all my Ubuntu files to that partition and shrunk the Ubuntu partition to the minimum. I set the GRUB bootloader to load Windows by default, and basically rarely/never touched the Ubuntu install again.
At the time, Microsoft was notifying users to approve the upcoming Windows 10 update ahead of time. I wasn’t getting that notification and kept running Windows update until I had all of the latest updates. I tried all the tricks and couldn’t get it to show. Eventually, I decided I would let it show on its own, which it did. Likely, Microsoft didn’t roll it out to my region at the time.
Previously, I mentioned the technical preview didn’t work. I tried again, multiple times and versions, all getting stuck at the boot logo. I thought, maybe it will be fixed by the time Microsoft rolls out the “RTM” 10240 build.
Guess what? On release day, I tried everything, it refused to accept the fact that it should be downloading something. What I did instead was the Windows Media Creation Tool to try to get it updated. It failed, both times. Boot logo.
I finally realized that the problem was that I had an older BIOS and it needed to be updated. I went into Windows 7 one last time, downloaded a BIOS update from the Lenovo website.
Then I successfully updated to Windows 10!
Today - I have had Ubuntu available, rarely/never using it. I finally got around to “fixing” the Master Boot Record using Windows to skip the ugly GRUB and go to the Windows bootloader. I deleted the partitions using Windows, and installed System Rescue CD to a USB because I knew it had GParted (partition tool). I booted the USB, entered “startx” at the terminal (remembered that Linux trick to get into the GUI), opened GParted, and made my Windows Partition bigger from the free space from the old partitions.
Next story: I transition myself from TrueCrypt 7.1a
0 notes